Linux iptables控制网络访问
一、IPTABLES基础用法
(1)iptables主要table
◆ filter
◆ nat
◆ mangle
(2)filter主要链
◆ INPUT
◆ OUTPUT
◆ FORWARD
1.1 简单设置方法
[root@server ~]# iptables -t filter -P OUTPUT DROP #禁止所有出向流量 [root@server ~]# iptables -t filter -P INPUT DROP #禁止所有入向流量 [root@server ~]# iptables -t filter -A INPUT -i lo -j ACCEPT # 放行所有回环口流量 [root@server ~]# iptables -L INPUT -v Chain INPUT (policy ACCEPT 70 packets, 5316 bytes) pkts bytes target prot opt in out source destination 0 0 ACCEPT all -- lo any anywhere anywhere | | | | 入口 出向 源 目的 [root@server ~]# iptables -t filter -A INPUT -p icmp -j ACCEPT # 放行icmp协议 [root@server ~]# iptables -t filter -A INPUT -p TCP --dport 22 -m state --state NEW -j ACCEPT | | -m 指定状态 NEW状态代表第一次握手进来的 [root@server ~]# iptables -t filter -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT | 放行ACK回包以及主动访问别人,别人的回包 注1:了解TCP的7种状态 [root@server ~]# vim /etc/sysconfig/iptables # 所有iptables配置都保持在这里
1.2 iptables规则查看技巧
[root@server ~]# iptables -L -v Chain INPUT (policy ACCEPT 99 packets, 4152 bytes) pkts bytes target prot opt in out source destination 2 102 ACCEPT all -- lo any anywhere anywhere 5307 396K ACCEPT icmp -- any any anywhere anywhere 9345 551K ACCEPT tcp -- any any anywhere anywhere tcp dpt:ssh state NEW 126K 18M ACCEPT all -- any any anywhere anywhere state RELATED,ESTABLISHED | 匹配规则的流量大小 [root@server ~]# iptables -L -v -n Chain INPUT (policy ACCEPT 99 packets, 4152 bytes) pkts bytes target prot opt in out source destination 2 102 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 5314 397K ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 9353 551K ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 state NEW 126K 18M ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED | -v与-n的区别 [root@server ~]# iptables -L -v -n --line-numbers Chain INPUT (policy ACCEPT 99 packets, 4152 bytes) num pkts bytes target prot opt in out source destination 1 2 102 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 2 5319 397K ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 3 9365 552K ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 state NEW 4 127K 18M ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED | 首行多了显示规则编号
1.3 保存iptables规则
# save规则时报错,原因是缺少iptables-services服务 [root@server ~]# service iptables save The service command supports only basic LSB actions (start, stop, restart, try-restart, reload, force-reload, status). For other actions, please try to use systemctl. # 安装iptables-services服务 [root@server ~]# yum install iptables-services -y [root@server ~]# service iptables save iptables: Saving firewall rules to /etc/sysconfig/iptables:[ OK ]
二、IPTABLES高级用法
2.1 通过type对包进行细致划分
(1)问题引入:规则颗粒度过粗
# 配置该规则,会导致client无法ping通server;server也无法ping通client [root@server ~]# iptables -A INPUT -p icmp -j DROP # 拒绝全部请求,请求包和回包都拒绝 [root@server ~]# ping www.baidu.com PING www.a.shifen.com (180.101.49.11) 56(84) bytes of data. ^C --- www.a.shifen.com ping statistics --- 3 packets transmitted, 0 received, 100% packet loss, time 2000ms [root@client ~]# ping server.starcto.com PING server.starcto.com (10.23.162.107) 56(84) bytes of data. ^C --- server.starcto.com ping statistics --- 2 packets transmitted, 0 received, 100% packet loss, time 999ms
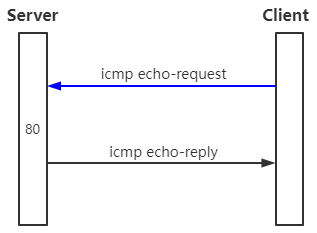
注:以icmp协议为例!!!
(2)通过type细分后
[root@server ~]# iptables -F # 清空规则 # 配置该规则,client无法ping通server;但server可以ping通client [root@server ~]# iptables -A INPUT -p icmp -m icmp --icmp-type echo-request -j DROP # 禁止icmp的请求包(echo-request),自然也不会有回包(echo-reply),但不影响server去请求别人,别人回包(echo-reply) 注:针对-m 对icmp进行详细匹配,--icmp-type echo-request为详细匹配类型!!! [root@client ~]# ping server.starcto.com PING server.starcto.com (10.23.162.107) 56(84) bytes of data. ^C --- server.starcto.com ping statistics --- 2 packets transmitted, 0 received, 100% packet loss, time 1000ms [root@server ~]# ping client.starcto.com # server ping测client发送的是echo-request,client回包是echo-reply。防火墙没有禁止echo-reply报文,所以server可以对外ping测 PING client.starcto.com (10.23.3.57) 56(84) bytes of data. 64 bytes from client.starcto.com (10.23.3.57): icmp_seq=1 ttl=63 time=1.10 ms ^C --- client.starcto.com ping statistics --- 2 packets transmitted, 2 received, 0% packet loss, time 1001ms rtt min/avg/max/mdev = 0.555/0.830/1.105/0.275 ms 注:icmp请求是由echo-request请求包和echo-reply回包组成。
(3)帮助文档使用技巧
[root@server ~]# iptables -A INPUT -p icmp -m icmp -h iptables v1.4.21 …… icmp match options: [!] --icmp-type typename match icmp type [!] --icmp-type type[/code] (or numeric type or type/code) Valid ICMP Types: any echo-reply (pong) # 回应 destination-unreachable network-unreachable host-unreachable protocol-unreachable port-unreachable fragmentation-needed source-route-failed network-unknown host-unknown network-prohibited host-prohibited TOS-network-unreachable TOS-host-unreachable communication-prohibited host-precedence-violation precedence-cutoff source-quench redirect network-redirect host-redirect TOS-network-redirect TOS-host-redirect echo-request (ping) # 请求 router-advertisement router-solicitation time-exceeded (ttl-exceeded) ttl-zero-during-transit ttl-zero-during-reassembly parameter-problem ip-header-bad required-option-missing timestamp-request timestamp-reply address-mask-request address-mask-replyt
2.2 通过状态对包进行细致划分
- NEW状态:说明这个数据包是收到的第一个数据包。
- ESTABLISHED状态:只要发送并接到应答,一个数据表的状态就从NEW变为ESTABLISHED,并且该状态会继续匹配这个连接后继数据包。
- RELATED状态:当一个数据包的状态处于ESTABLISHED状态的连接有关系的时候,就会被认为是RELATED,也就是说一个连接想要是RELATED状态,首先要有一个ESTABLISHED的连接。
- INVALID状态:不能被识别属于哪个连接状态或没有任何关系的状态,一般这种数据包都是被拒绝的。
示例1:ICMP协议
- icmp echo-request为NEW状态
- icmp echo-reply为ESTABLISHED
(1)修改INPUT默认策略方法
[root@server ~]# iptables -A INPUT -p tcp --dport 22 -j ACCEPT # 放行22端口请求 [root@server ~]# iptables -A INPUT -i lo -j ACCEPT # 放行回环口请求 [root@server ~]# iptables -P INPUT DROP # INPUT默认策略为DROP # 可以看到,client已经无法ping通server了 [root@client ~]# ping server.starcto.com PING server.starcto.com (10.23.162.107) 56(84) bytes of data. ^C --- server.starcto.com ping statistics --- 2 packets transmitted, 0 received, 100% packet loss, time 999ms
状态匹配帮助文档用法
[root@server ~]# iptables -t filter -A INPUT -p icmp -m state -h iptables v1.4.21 …… state match options: [!] --state [INVALID|ESTABLISHED|NEW|RELATED|UNTRACKED][,...] State(s) to match
[root@server ~]# iptables -t filter -A INPUT -p icmp -m state --state NEW -j ACCEPT # 放行状态为NEW的 # 发现客户端已经可以ping通,但只能ping通一个包;所以猜测第二个报文不是NEW状态,而是ESTABLISHED状态 [root@client ~]# ping server.starcto.com PING server.starcto.com (10.23.162.107) 56(84) bytes of data. 64 bytes from server.starcto.com (10.23.162.107): icmp_seq=1 ttl=63 time=0.950 ms # 对上述猜想进行验证 [root@server ~]# iptables -t filter -D INPUT -p icmp -m state --state NEW -j ACCEPT # 先删除NEW状态规则 [root@server ~]# iptables -t filter -A INPUT -p icmp -m state --state NEW,ESTABLISHED -j ACCEPT # 放行NEW状态与ESTABLISHED状态 # 放行NEW和ESTABLISHED状态后,发现client可以持续ping通server [root@client ~]# ping server.starcto.com PING server.starcto.com (10.23.162.107) 56(84) bytes of data. 64 bytes from server.starcto.com (10.23.162.107): icmp_seq=1 ttl=63 time=1.00 ms 64 bytes from server.starcto.com (10.23.162.107): icmp_seq=2 ttl=63 time=0.428 ms 64 bytes from server.starcto.com (10.23.162.107): icmp_seq=3 ttl=63 time=0.425 ms ^C --- server.starcto.com ping statistics --- 3 packets transmitted, 3 received, 0% packet loss, time 2000ms rtt min/avg/max/mdev = 0.425/0.620/1.008/0.274 ms
注:以上测试可以看出,ping测只有一个包的状态是NEW,从第二个ping包开始都是ESTABLISHED状态!!!
(2)修改OUTPUT默认策略方法
[root@server ~]# iptables -A OUTPUT -p tcp --sport 22 -j ACCEPT [root@server ~]# iptables -P OUTPUT DROP # OUTPUT默认策略为DROP # 发现client无法ping通server,所有的回包都被拒绝 [root@client ~]# ping server.starcto.com PING server.starcto.com (10.23.162.107) 56(84) bytes of data. ^C --- server.starcto.com ping statistics --- 2 packets transmitted, 0 received, 100% packet loss, time 999ms [root@server ~]# iptables -A OUTPUT -p icmp -m state --state ESTABLISHED -j ACCEPT # 放行ESTABLISHED状态 # 发现client可以正常ping通server,由此可见server的回包都为ESTABLISHED状态 [root@client ~]# ping server.starcto.com PING server.starcto.com (10.23.162.107) 56(84) bytes of data. 64 bytes from server.starcto.com (10.23.162.107): icmp_seq=1 ttl=63 time=1.20 ms 64 bytes from server.starcto.com (10.23.162.107): icmp_seq=2 ttl=63 time=0.389 ms ^C --- server.starcto.com ping statistics --- 2 packets transmitted, 2 received, 0% packet loss, time 1001ms rtt min/avg/max/mdev = 0.389/0.794/1.200/0.406 ms
注:由此可见,在整个ping过程中,只有第一个包为NEW状态,其余的所有请求与回应包都为ESTABLISHED状态!!!!
示例2:TCP协议
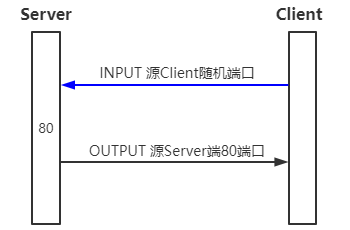
三次握手过程中:Client第一请求是NEW状态,剩下Server回复和Client再次请求都是ESTABLISHED状态。
(1)Server80端口对外提供服务(Client->Server)
[root@server ~]# iptables -A INPUT -p tcp --dport 22 -j ACCEPT # 放行入向目的端口22端口请求 [root@server ~]# iptables -A OUTPUT -p tcp --sport 22 -j ACCEPT # 放行出向源端口为22的请求 [root@server ~]# iptables -P INPUT DROP # INPUT默认策略为DROP [root@server ~]# iptables -P OUTPUT DROP # OUTPUT默认策略为DROP [root@server ~]# iptables -A INPUT -p tcp --dport 80 -m state --state NEW,ESTABLISHED -j ACCEPT # 放行入向NEW与ESTABLISHED状态 [root@server ~]# iptables -A OUTPUT -p tcp --sport 80 -m state --state ESTABLISHED -j ACCEPT # 放行出向ESTABLISHED状态
注:由于我的规则设置比较严格,默认没有放行的INPUT与OUTPUT请求全部DROP,所以,需要严格定义每一条规则!!!
(2)Server访问外部DNS53端口(ServerA访问ServerB)
[root@server ~]# iptables -A OUTPUT -p udp --dport 53 -j ACCEPT # server请求53端口,是出向(OUTPUT),目的端口是53 [root@server ~]# iptables -A INPUT -p udp --sport 53 -j ACCEPT # 来自53端口的回包,对于server来说是入向(INPUT),对应server来说回包的源端口是53
作者:UStarGao
链接:https://www.starcto.com/service_operations/275.html
来源:STARCTO
著作权归作者所有。商业转载请联系作者获得授权,非商业转载请注明出处。
UCloud云平台推荐
随便看看
- 2021-03-28Hadoop伪分布式系统搭建
- 2021-07-13开源文档管理系统Wizard容器化部署教程
- 2021-04-23Linux 预防SSH暴力破解神器—DenyHosts
- 2022-01-15K8S Pod模板介绍
- 2021-11-19Windows云主机服务器高频配置集锦



